OAuth has evolved a lot since 2012 with many “lessons learned”. AAuth (Agent Auth) is an attempt to bring those lessons together for AI agents. AAuth is an exploratory spec from Dick Hardt (Author/Co-Author of OAuth 2.0, 2.1)
What started as OAuth 2.0 has grown into dozens of supporting RFCs, drafts, and practical implementations: PKCE, DPoP, Token Exchange, Rich Authorization Requests (RAR), JAR, JARM, OAuth 2.0 mTLS, Pushed Authorization Requests (PAR), and more. Each one addresses a real gap. Each one moves the ecosystem forward. But taken together, they also show something else: the original model wasn’t built for the systems we’re building today.
We are building autonomous agents which make decisions on their own, calling other agents, APIs and MCP servers. We have multi-hop user delegation. We have AI systems making decisions on behalf of users. We have MCP tool invocation where identity, delegation, and proof-of-possession matter. We’ve bolted improvements onto OAuth to handle these realities, but the patterns are scattered across specs, profiles, and drafts.
AAuth (Agent Auth) brings together authentication, authorization, a number of OAuth RFCs and combines with message signing and discovery to provide the foundation of agent identity and access management.
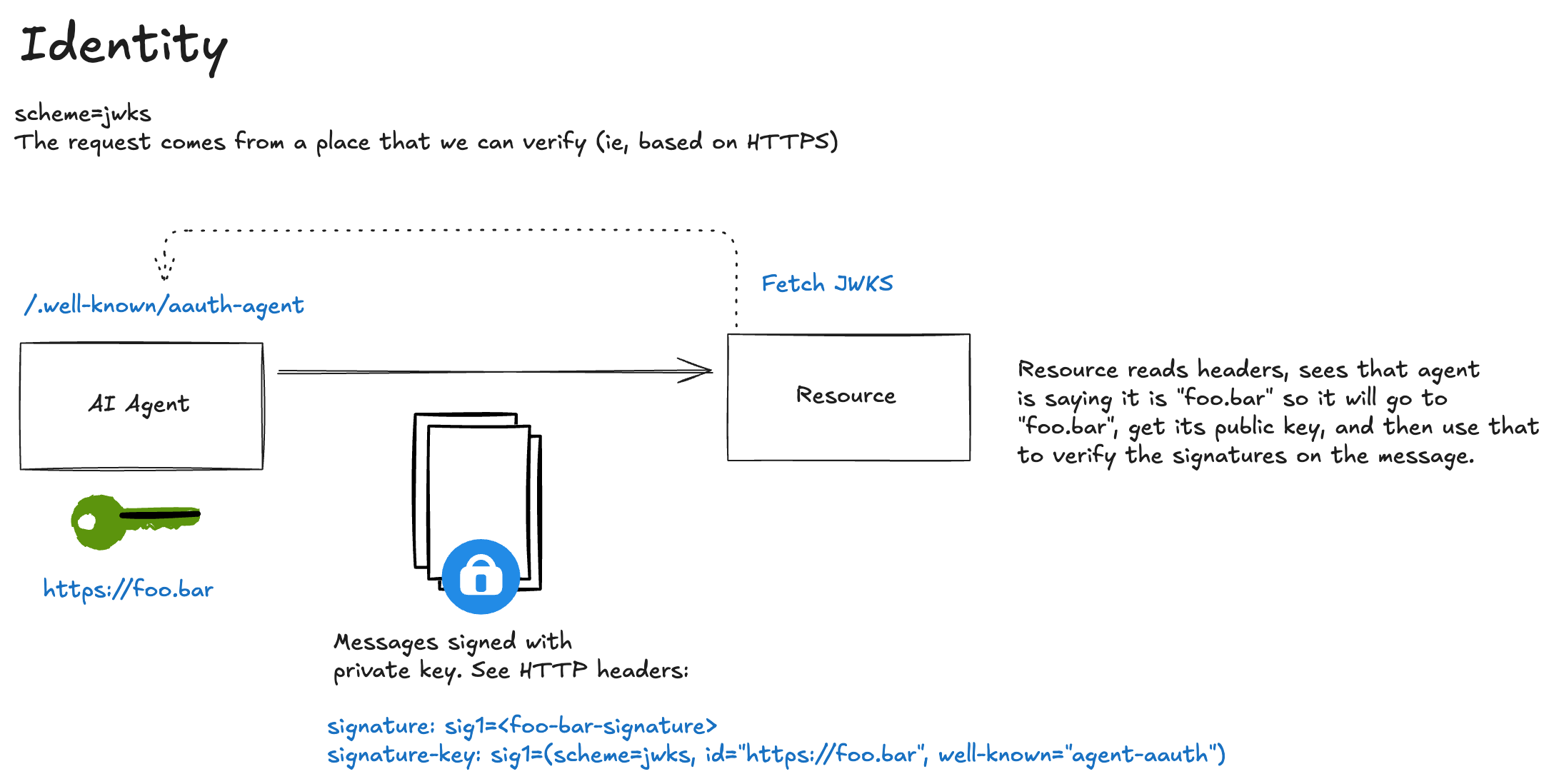
With AAuth, we can:
- get rid of bearer tokens
- make agent identity cryptographically verifiable
- provide a progressive scale for auth: starting with pseudonymous, advancing to stable identity, and then authorization/user/obo etc
- dynamically discover permissions to request
- bind permission requests to agents cryptographically
- support rich authorizations
- support agent identity delegation / distributed deployments
- tie in with existing identity standards (SPIFFE/WISME, etc) where it makes sense
AAuth is not a replacement for OAuth. It’s not a new standard (at the moment). It’s an exploration of what authentication and authorization could look like if we started from the perspective of agent-to-agent communication, cryptographic identity, proof-of-possession by default, and unified authn/authz semantics.
In AAuth, agents are first-class identities, require signed HTTP messages, unify identity and authorization into one protocol, and make delegation explicit and verifiable. Instead of bearer tokens waiting to be exfiltrated, every request is signed. Instead of tokens representing either a user or an application, AAuth tokens can represent both simultaneously. Instead of bolting token exchange onto the side, delegation chains become visible and enforceable.
How does it all work? I encourage you to read the draft exploratory spec. And then take a look at how it works in a real(istic) environment (next section).
Full Working Prototype
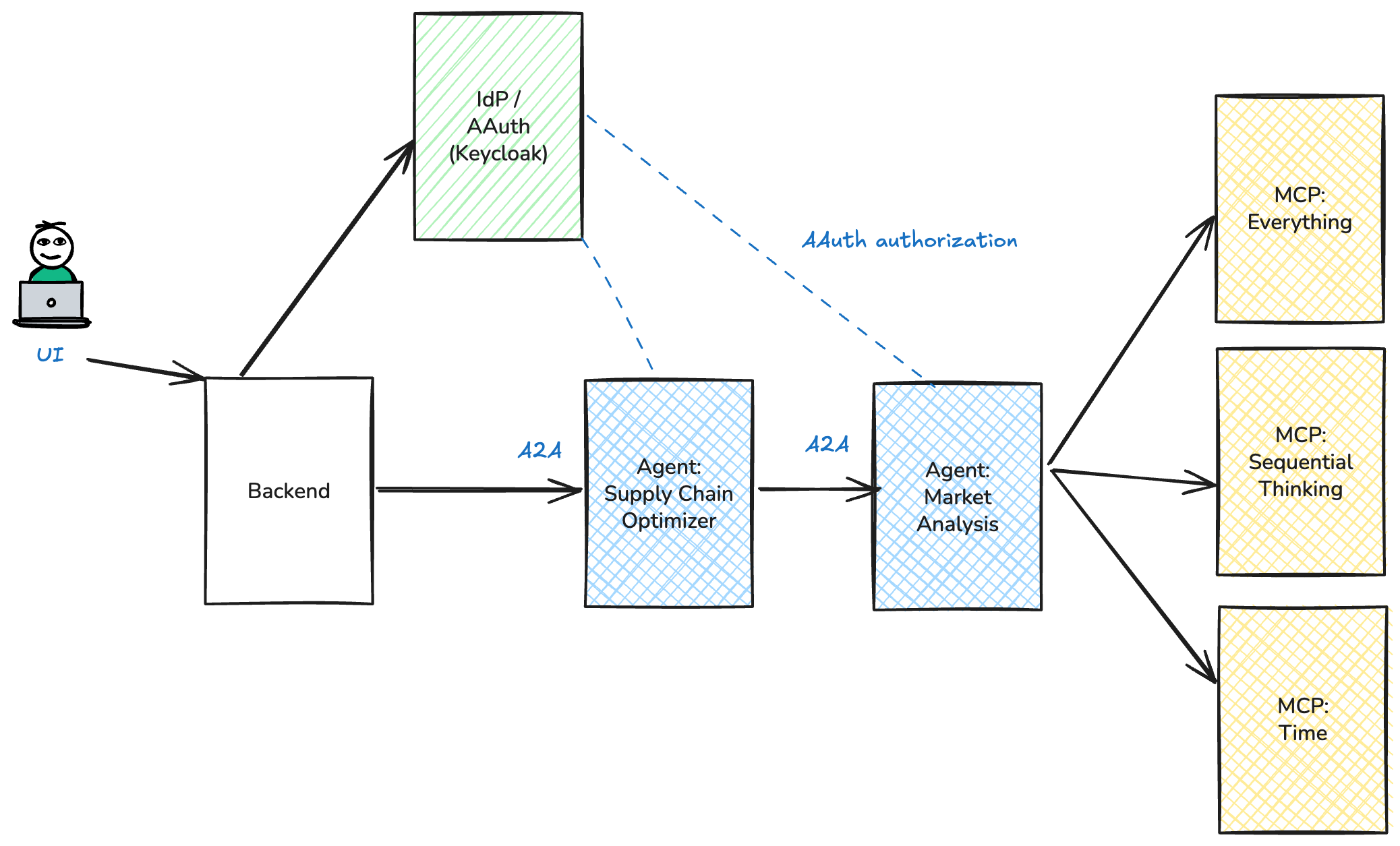
It starts with agent identity established via JWKS and HTTP message signing. A backend signs requests, downstream agents verify identity via discovery, and an agentgateway enforces signature policies. Then it moves into autonomous authorization, where a resource challenges with a resource token, the caller exchanges it at Keycloak, and retries with a bound authorization token. Then it adds user-delegated authorization, where user consent is required and the resulting token carries both the user’s identity and the agent’s identity. Finally, it shows how Agentgateway can act as a policy enforcement point, applying CEL-based policies to AAuth claims, validating delegation chains, and enforcing scopes and audiences centrally.
If you’re building AI agents, MCP-style systems, or any form of agent-to-agent infrastructure, you should care about three things: who is calling, on whose behalf, and can they prove it cryptographically. OAuth continues to evolve, and that’s a good thing. AAuth is an attempt from Dick Hardt to synthesize where we are, simplify the model, and push forward patterns that matter for agentic and AI-native systems. I am going to be following the evolution of this very closely.
